Most recent News & Articles
Rich rewards in the mobility sector trigger a scramble for scale
To succeed in the mobility business, companies need scale – and they need it fast. Representatives from Spanish financial services firm CaixaBank, vehicle manufacturer Kia in Slovenia and UK online platform provider Finalrentals discuss how they are ramping up their mobility businesses.
The 2024 Qorus-Infosys Finacle Banking Innovation Awards submission guide
The Qorus-Infosys Finacle Banking Innovation Awards are open for entries until June 21, 2024. Here's a guide to everything you...
CaixaBank Private Banking opens exclusive center in Barcelona
With over €10,300 million in global assets set to be managed from this location, approximately 80 specialists will provide independent...
MAAF Assurances launches "Home Run" experience on Fortnite to promote road safety
With "Home Run," MAAF aims to offer young gamers a unique and entertaining experience while teaching them essential driving skills.
Breaking barriers: Banca Widiba's quest for gender equality in finance
Banca Widiba in Italy takes the issue of gender equality very seriously. In fact, its recent study on the subject...
NAB offers free cyber defense to small businesses
NAB, Australia’s largest business bank, is urging small businesses to prioritize cybersecurity, announcing a year of free cyber security software...
Chubb to acquire Healthy Paws, a leading pet insurance provider
Chubb, the global insurance giant, has announced its definitive agreement to acquire Healthy Paws, a U.S.-based pet insurance provider, from...
Most recent Studies & Reports
Driving forces: The interplay of financial services and the EV sector
The financial services sector and the electric vehicle (EV) sector are two dynamic realms undergoing a significant transformation in today's...
A bancassurance breakthrough: Nurturing SME relationships through customized insurance products
In this paper, we outline the opportunity bancassurance presents to banks, as well as the key considerations that should be...
Innovation Radar: Reinvention Awards Europe winners 2024
Discover the most innovative projects from banks and insurance companies in Europe.
Unleashing SME banking potential with embedded finance: Simplifying financial services to create unprecedented convenience for SMEs
In this paper, we will unravel the key challenges that banks need to address to not only navigate the upcoming...
Latest innovations
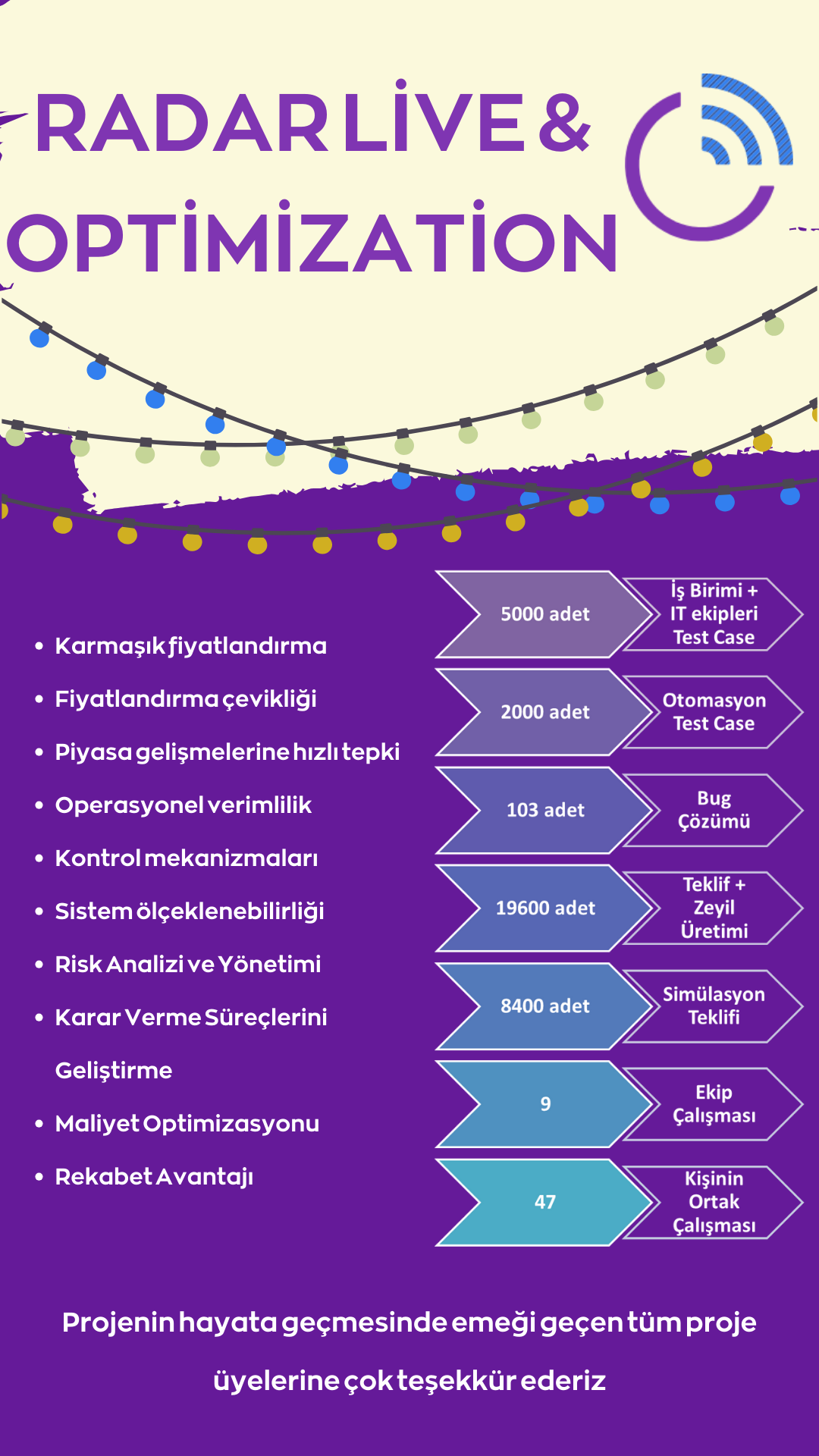
Radar Live & Optimization
Through the integration of our Radar Live tool, a significant step has been taken by enabling the direct integration of...
Fully immersive - the VR-based insurance advice app. Customers and advisors meet in the Metaverse
By 2016, almost 3 million VR glasses had been sold worldwide. Five years later the amount had increased almost sevenfold....
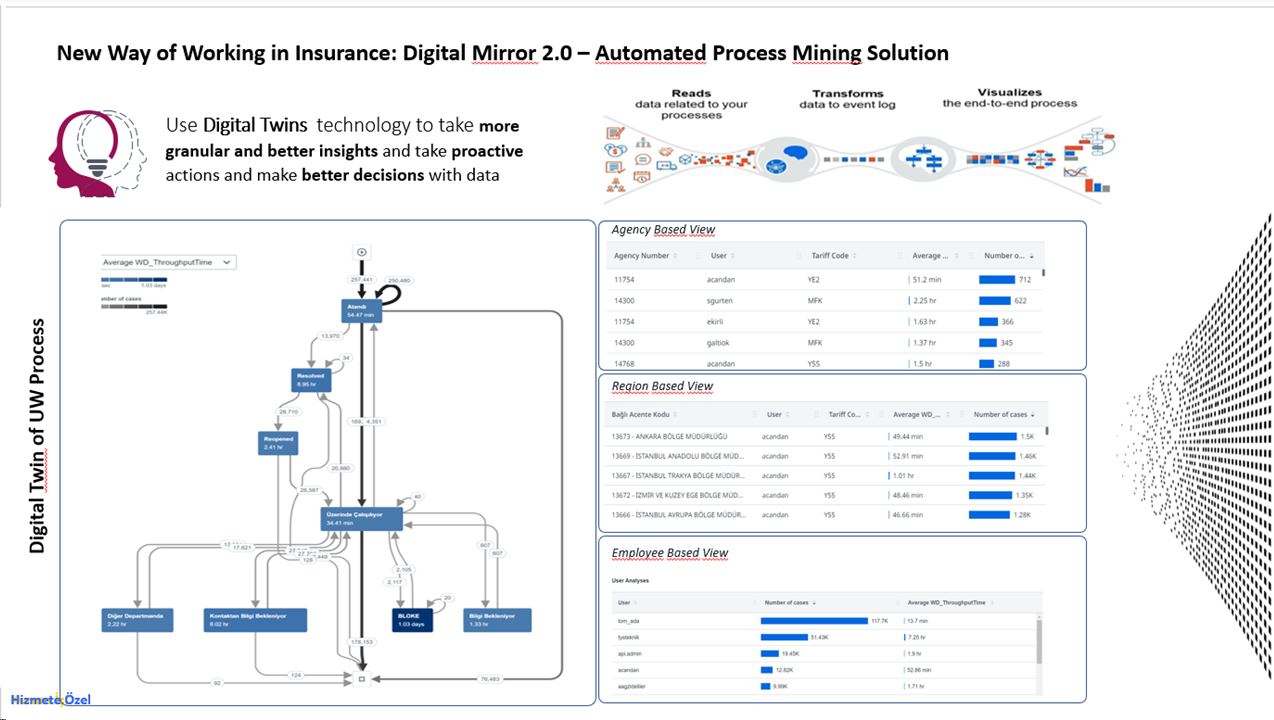
TwinTrack Analytics
The Digital Mirror Project, developed in 2023, embarked on a vision to digitize and make trackable the repetitive and labor-intensive...
OneZurich Workforce Ambassador Module
Background: In 2021, we launched our Employee Ecosystem Initiative (OenZurich) aimed at revolutionizing the digital experience for our workforce. Over...

Join the Qorus
Today, Qorus is a catalyst for reinvention for our financial services members by helping them to go further, be faster and work together.
Forthcoming events
Cybersecurity: The role of the banks and insurance
Examine symbiotic relationships between financial institutions and embedded cybersecurity insurance, emphasizing collaborative efforts against digital risks and cyber threats. This session organized with our partner Allianz Partners, will explore the complexities of cybersecurity within the financial services industry and discuss effective cyber risk management practices. Invited experts will examine how...
Technology-driven sustainable synergy: Maximizing the Impact of green finance and IT solutions
Discover the powerful synergy between green finance and IT solutions, driving global sustainability through innovative collaborations. Position your organization as a leader in building a greener future by leveraging this dynamic alliance to contribute to a sustainable world.
Reinvent Forum Lisbon
Reinvent Forum Lisbon - is dedicated to the digital transformation influencing the insurance sector. Our event brings together industry leaders, experts, and innovators to delve into the latest trends and strategies for enhancing customer satisfaction through innovative digital endeavors. Attendees can expect profound insights into the evolving landscape of insurance.
Electric vehicle charging
Future position of insurance in mobility will be shaped by ongoing technological advancements, changing consumer behavior, and evolving regulatory frameworks. One of the key roles of insurance in mobility will be to provide coverage for new and emerging risks associated with the use of new technologies, such as autonomous vehicles...
Climate change and insurance gap
Climate change intensifies the insurance gap, driving a surge in extreme weather events and economic losses. Join our online event to collaborate on building a more resilient future in the face of climate change.
We help banks and insurers to reinvent themselves to thrive.
 Further
Further
We curate inspiring and innovative projects, technology and ideas so individuals, teams and organisations can collectively create the future of financial services.
 Faster
Faster
We’re a catalyst for reinvention, improving revenue generation, creating efficiencies, redefining customer experiences and forming profitable relationships.
 Together
Together
We're a neutral space where members unite to share, learn and collaborate, thinking freely to solve problems through an ecosystem of unique, specialist communities.















.png)


